With the rise of the Internet and IT networks, many solutions today work over IP. Whether video surveillance, access control, or attendance time management, all this equipment uses IP technologies to communicate and operate. As with any network, time synchronization is essential, not only to ensure the proper functioning of monitoring systems, but also to ensure accurate and chronological timestamping of events.
Time synchronization makes sure equipment works correctly.
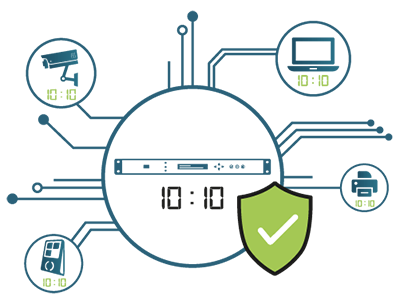
With the rise of the Internet and IT networks, many solutions today work over IP. Whether video surveillance, access control, or attendance time management, all this equipment uses IP technologies to communicate and operate.
As with any network, time synchronization is essential, not only to ensure the proper functioning of monitoring systems, but also to ensure accurate and chronological timestamping of events. (e.g. video surveillance footage as evidence in an investigation).
The best way to synchronize equipment on an IP network (cameras, access readers, clocking terminals, computers, printers) is to use the standard NTP protocol.
What happens when an IP-based solution is out of sync?
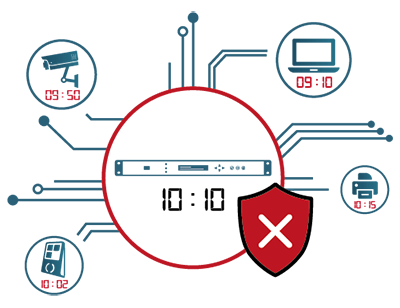
Let’s take a concrete example of an inaccurate timestamp on a video surveillance system:
A video shows an employee sneaking into an area of a building. In the same area, IT equipment (computer) was stolen and disconnected from the network. Yet the company cannot demonstrate that the employee is responsible for the theft.
Why?
Because the history of the computer system shows that the computer was disconnected before (e.g. 9:10 am) the time the employee is seen entering the area on the video (9:50 am).
This company could have easily solved this serious security problem by using a time server that distributes a reference time over its entire network infrastructure.
Tracing events with an NTP/PTP time server
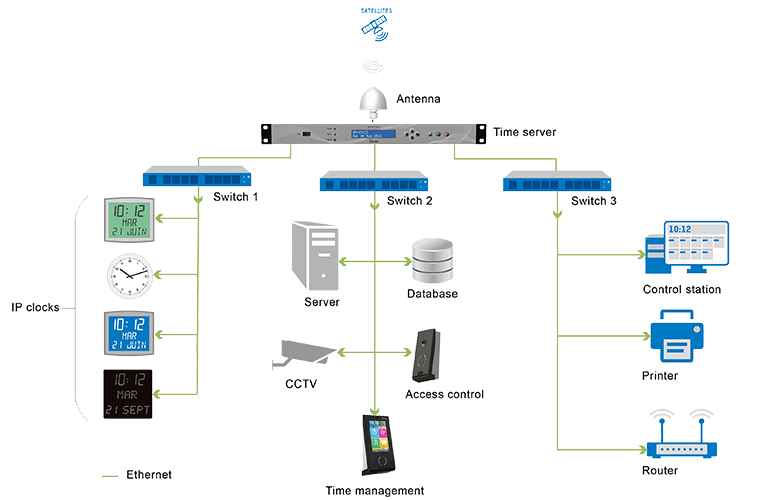
A NTP time server enables precise timestamps for video surveillance systems, access control systems, time and attendance, alarms and other network infrastructure elements (routers, firewalls, etc.).
Traceable time stamps provide the necessary evidence for legal actions.
The server works securely behind the firewall to synchronize all network hardware and software, including system logs.

