In many applications, including time synchronization, GNSS is now commonplace. The best known constellation is GPS. However, all these GNSS systems share a common vulnerability: the signals transmitted by these satellites are very weak. GNSS satellites operate from the Earth’s orbit. The transmitted signal is extremely weak when it reaches the earth’s surface. This low signal strength at the receivers makes GNSS use susceptible to intentional (malicious) or unintentional interference.
What is GNSS?

In many applications, including time synchronization, GNSS (Global Navigation Satellite System) is now commonplace. The best known constellation is GPS.
However, all these GNSS systems share a common vulnerability: their signals are very weak.
GNSS satellites operate from the Earth’s orbit. The transmitted signal is extremely weak when it reaches the earth’s surface. This low signal strength at the receivers makes GNSS use susceptible to intentional (malicious) or unintentional interference.
GNSS jamming
Jamming is the presence of a competing signal that prevents the GNSS receiver from decoding the real satellite signal.
Jamming from other sources of radio transmission can be intentional (malicious) or unintentional.
Unintentional jamming: Radar or communication transmitters, although operating in a different frequency band, may interfere with GNSS reception due to their scattering power.
Intentional jamming: GNSS jammers, although illegal in most countries, are readily available on the Internet. Announced as privacy jammers, they can disable GNSS reception over several kilometres
Signal spoofing
Spoofing is the intentional transmission of fake GNSS signals to divert users from their real position.
Spoofing requires sophisticated equipment to recreate satellite signals. Spoofing is more difficult to detect than jamming.
What solutions to protect against jamming and spoofing?
Jamming is relatively easy to detect, and there are several ways to prevent it. Detecting spoofing is more difficult, especially when using a high quality spoofing equipment.
Bodet offers several solutions to minimise these effects and guarantee optimal synchronization.

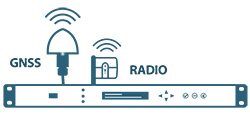
Example 1: A robust antenna with software detection

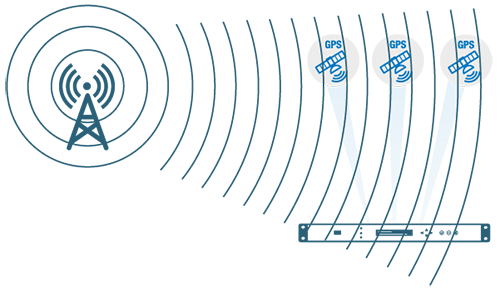
Example 2: Remote multi-site installation
Jamming or spoofing is difficult because of the distance between sites. Synchronisation between servers via private network.
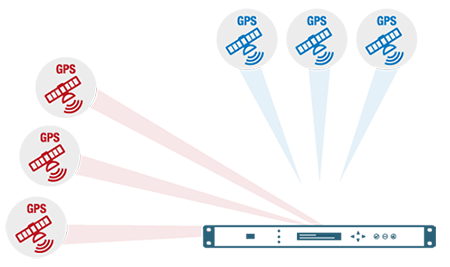
Example 3: Multi-source installation
The server analyses satellite and radio signals in real time and compares them with its high-performance time base. This way, it can detect any discrepancy.

